Setup Enterprise Connector
You will be using the Alef Mobile Network API to carry out the tasks in this section. This is a basic config, Refer to the API reference documentation to learn more about the API and explore the full schema.
Enterprise Mobile Gateway Concept
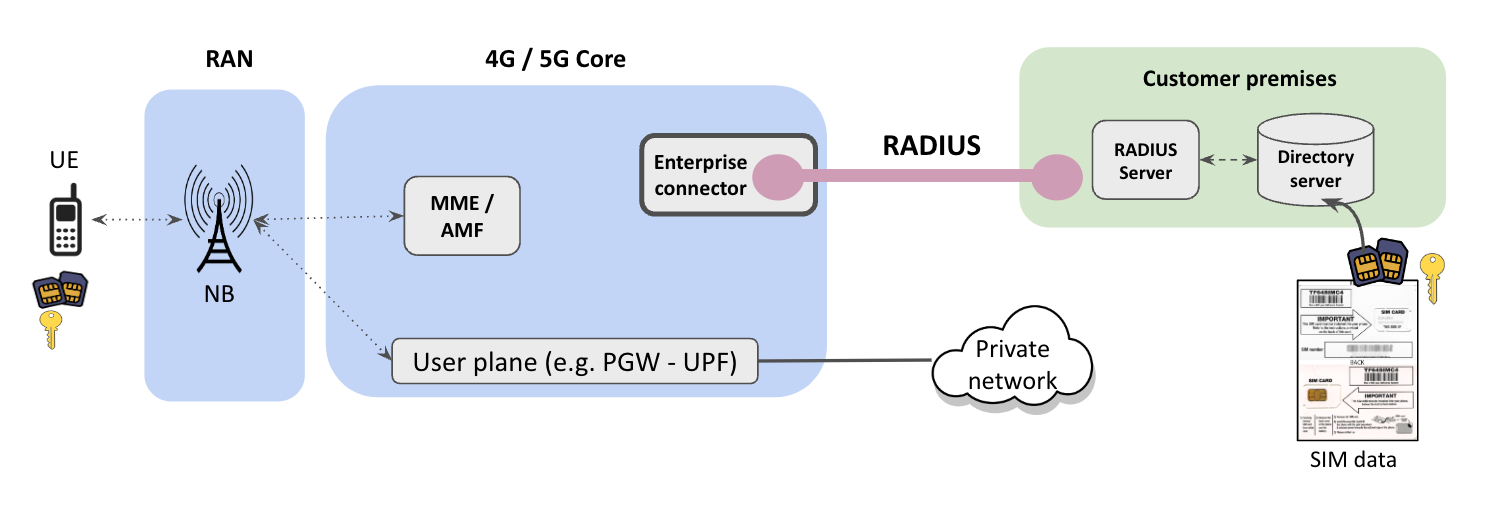
The Enterprise Mobile Gateway allows you to use an enterpise IAM to store and manage all your SIM data. The Authentication and Authorization is transfered from the Mobile Core to your IAM system. This allows for setting IP addresses, policies and activily manage connections with Change of Authorization or Disconnect request.
Radius Client
The Enterprise Mobile Gateway is a radius client. The radius client communicates with your radius server via the network connection between your network and Alef.
For this it uses the radius client's IP address (nas-ip-address), which is typically the same as the MME IP address. The client will be configured like any other radius client with
a shared key and nas-identifier (default to Mobius) to handle its authentication against your IAM.
Radius Server
One or more Radius servers can be configured per Enterprise Mobile Gateway. This configuration is for the Radius Client to know which servers it can connect to and what the priority of each server is. Each server will require the IP address to be configured. This IP address needs to be addressable from the Alef network via the network connection to your network. The other configuration details are standard for a radius server connection and explained below
Dynamic Authorization
In order to enable dynamic authorization on your Enterprise Mobile Gateway, the ability to support Change of Authorization (CoA) or Disconnect requests, you need to specify the server that can instruct the Enterprise Mobile Gateway to manage connections. This function requires the Enterprise Mobile Gateway to be configured with the server information from which it can accept incoming CoA/Disconnect requests. The configuration details are explained below
You will need to ensure that your IAM can operate with the Enterprise Mobile Gateway radius client. We can provide guidance on this. The solution has been tested using either OpenLDAP or MS Active Directory as LDAP databases, and either Cisco ICE or freeradius-server as radius servers.
SIM Provisioning
If you are using the Enterprise Mobile Gateway you will need to provision your SIMs and keys into your IAM. Alef can provide you with the VSA (Vendor-Specific attributes) and an LDAP schema for this.
Configure your Enterprise Mobile Gateway
Required information
- name: Name for the Enterprise Mobile Gateway, needs to be unique in your account. At least one of these two needs to be set:
- nas-ip-address: NAS IP address, can be the MME IP.
- nas-identifier: NAS Identifier name for Radius Client (Default Mobius).
Optional:
- framed-mtu: MTU Frame size (Default 1432).
- auth-server: See below for details.
- dynamic-authorization: See below for details.
Please contact Alef Support if you have any questions relations to these items.
You will use the following POST request body with the /connectivity/v2/networks/radius endpoint to create and configure your Enterprise Mobile Gateway.
You can use the following GET request body with the /connectivity/v2/networks/radius/:id endpoint to retrieve your Enterprise Mobile Gateway information.
Expand here to see the mobile core POST request body.
{
"name": "string",
"nas-ip-address": "IP address",
"nas-identifier": "Mobius",
"framed-mtu": 1432,
"auth-server": [
{
"name": "Name",
"host": "IP address",
"port": 1812,
"shared-key": "string",
"priority": 0,
"transport-config": "UDP",
"reconnect-timer": 0,
"dead-interval": 0,
"send-status-server": false
}
],
"dynamic-authorization": {
"allowed-client": [
{
"address": "IP address",
"shared-key": "string",
"allow-coa-requests": true,
"allow-disconnect-requests": true
}
]
}
}
The following section is a breakdown of the request:
Enterprise Mobile Gateway POST request guide
Authentication and Authorization servers
This is the required information to configure your IAM server(s) as an endpoint for the Enterprise Mobile Gateway:
- name: Name of the Radius server.
- host: IP address of the Radius server.
- port: Port of the Radius server (default 1812)
- shared-key: Shared key for the Radius server.
- priority: Priority of the server. 0 disables the server. Higher number is a higher priority (max 255).
- transport-config: The Radius transport protocol between server and client. Options are UDP/TCP, default to UDP.
Optional values:
- reconnect-timer: Time after which we attempt to reconnect to a server in case of errors (default 15s).
- dead-interval: Interval in seconds after which a server is declared unreachable (default 30s).
- send-status-server: Whether to send status server messages (default false).
"auth-server": [
{
"name": "string",
"host": "IP address",
"port": 1812,
"shared-key": "string",
"priority": 1,
"transport-config": "UDP",
"reconnect-timer": 15,
"dead-interval": 30,
"send-status-server": false
}
],
Dynamic Authorization
This is the required information to configure your IAM server(s) as allowed servers to make an inbound request to the Enterprise Mobile Gateway:
- address: IP address of the Radius server.
- shared-key: Shared key for the Radius server.
- allow-coa-requests: Enable Change of Authorization requests (default true).
- allow-disconnect-requests: Enable disconnect requests (default true).
"dynamic-authorization": {
"allowed-client": [
{
"address": "IP address",
"shared-key": "string",
"allow-coa-requests": true,
"allow-disconnect-requests": true
}
]
},